In this post, we’ll discuss what are DDoS attacks, their types, their major causes, how to detect them, and how to mitigate a DDoS attack. Keep reading till the end.
With the rise of the Internet, cyber-attacks are skyrocketing too. Let alone last year, roughly around 7,00,000 cyber attacks and cyber crimes were reported.
While some cyber attacks are mild and some are severe. One such severe attack is Distributed Denial-of-Service attack or DDoS attack.
If you’re willing to learn ethical hacking, here are the 11 best ethical hacking learning websites.
What is DDoS Attack?
A Distributed Denial of Service attack is a synchronized attack done using a large network of infected machines, called Botnet, to send coordinated traffic which exhausts the network resources of the victim. The objective is to bombard network resources such as memory, CPU, and link bandwidth by sending mass requests from the botnet.
As a result, the network (or app and website) is unable to perform user requests and refuse to respond to incoming traffic.
DDoS attacks are catastrophic and can bring down a server or network and create havoc. One can easily find and rent botnets on the black market to perform a DDoS attack. The bots in the botnet are controlled using a botnet architecture and a command-and-control system, which may be based on Peer-to-Peer (P2P), Internet Relay Chat (IRC), and HyperText Transfer Protocol (HTTP), or Domain Name System (DNS).
In a DDoS attack, the victim can range from a single web server to the Internet connection of an entire university, an entire city, or even an entire country. The interesting fact is that the users of the devices that participate in a DDoS attack are unaware of such attacks.
Related: 5 Best Ways To Keep Private Data Safe Online
How do DDoS attacks work?
Generally, four players participate in a successful DDoS attack – Attackers, Handlers, Agents, and victims.
The master or the attacker initially attempts to bring some hosts in a network under its control by compromising them.
The handlers include some malicious software (like malware) residing on remote machines that are used by the attacker. The purpose of choosing a set of victimized computers (handlers) to launch DDoS attacks is mainly to overcome the possibility of tracing the attack back to the attacker (client).
The agents, the third set of players are practically responsible for performing the attack. They typically consist of software on compromised machines through which the attack is performed.
Finally, the victim, the fourth player, maybe a single target machine, server, or network of many machines.
Also read: 5 Best IT Security Software (Full Automation)
Most Common DDoS Attacks
Here are the most common DDoS attacks.
1. SYN Flood DDoS Attack

Under this type of attack, the aim is to take advantage of the weakness in the TCP connection sequence (the three-way handshake). The attacker sends mass SYN requests to the victim’s server which exploits the limited slots and overloads them and ultimately resulting in the denial of service.
2. NTP Amplification

Under this attack, the attacker aims to bombard the victim’s network resources by amplifying the file size multiple times than the original ones. The larger the file, the larger the resources it needs and ultimately resulting in the denial of service.
3. Slow loris
Under the Slowloris attack, the client opens a connection and sends a request, the listener opens a socket and a new connection is established, and then another, and then another, and so on. The attacker exploits the process-based model but opens a number of concurrent connections and holds them open for as long as possible with the least amount of bandwidth possible which ultimately results in the denial of service.
4. Ping of Death

In the ping of death attack, when the larger IP packet has to be transferred, it has to be split into multiple small fragments. But the attacker manipulates the size of the packet. The recipient host reassembles the small fragments into one packet. But due to the manipulation, the recipient receives a larger packet upon reassembling. Thus it overflows the memory allocated to the packet and ultimately results in the denial of service.
Also check: Best Way To Protect Websites From Hackers
Major Causes of DDoS Attacks
These are the major causes of DDoS attacks.
1. Easy Availability of Tools
The easy accessibility of a large number of attack tools floating in the public domain is one of the major causes for networks or organizations frequently coming under DDoS attacks.
Evolution of new DDoS attack tools, several noble, and practical machine learning approaches have been used for DDoS attack detection and prevention. One such tool used for hacking is Burpsuite.
2. Vulnerable Architecture of the Internet
The pregnable architecture of the Internet is another major cause, allowing the attacker to easily spoof the source IP (SIP) addresses of attack packets, thus making it more difficult to detect the attack.
Further, the detection of malicious traffic becomes even harder, if its size and pattern are similar to those of legitimate traffic, making malicious traffic unobtrusive.
3. Trouble-Free Availability of Botnet
Another major cause is the easy availability of botnets in the black market. One can easily rent a botnet consisting of millions of Internet of Things (IoT). The botnet is available to rent for a specific time like for a week and one or two attacks.
Also read: Best Way To Surf Public WiFI Securely
Detection Techniques for DDoS Attacks
Here are the 7 detection techniques for the distributed denial-of-service attack.
1. Misuse Detection
Misuse detection searches for definite patterns (i.e., signatures, rules, or activities) in the captured network traffic to identify previously known DDoS intrusion types. Such detection techniques usually exhibit high detection rates with low numbers of false alarms. However, a misuse detection technique fails to detect unknown DDoS intrusion types.
2. Anomaly-based Detection
Anomaly-based detection techniques aim to identify new intrusion types in addition to the detection of known types. Such techniques analyze network traffic behavior and attempt to detect unusual patterns at an early stage. The three main symptoms of a DDoS attack are as follows – 1. A website becomes extremely slow. 2. A website does not load at all. 3. When a website becomes unavailable.
3. IP Traceback
As discussed earlier, in a DDoS attack, attackers mostly use zombies or reflectors to send attack packets to the victim’s machine using spoofed IP addresses. One can attempt to detect the attack source manually as well as automatically. It may be performed either at the victim end or from intermediate routers and traced back to the original source end.
4. Link Testing
In link testing, the victim conducts a test on each of its incoming links as a probable input link for DDoS attack traffic. If the test result is positive, it contacts the upstream router(s) closest to the victim. The contacted router then initiates an interactive traceback process recursively with its upstream routers until the true source of the attack is identified.
5. Packet Marking
Packet marking is a significant recent addition to the techniques used for the identification of the origin of DDoS attacks. In a packet-marking scheme, routers mark forwarding packets either deterministically or probabilistically, with their own addresses. So, when an attack occurs, the victim uses the marked information associated with the packet to trace back to the attack source.
6. Packet Logging
In the packet logging approach, routers store packet information so that such information can be used to trace an attack long after the attack has been completed. One can use data mining techniques on the logged packet data to determine the path that the packets may have traversed.
7. ICMP Traceback Messages
In this mechanism, the router generates ICMP traceback messages that include the content of forwarded packets along with information about adjacent routers and sends them to the destination. When flooding attacks occur, the victim uses these ICMP messages to construct attack graphs back to the attacker. The traceback messages help the victim find the original source of the attack.
Related: Cyber Security: An Ultimate Guide [2022 Update]
Prevention From DDoS Attacks
No matter what you think, there is no foolproof method to stop a DDoS attack. With the advancement of technologies, hackers are also finding new ways to attack that no one can detect and prevent. But still, there are some ways through which you stop these attacks or minimize your loss. Let’s see what are some ways through which you can secure your system.
First, I have mentioned the proactive steps you should take before an actual attack takes place. The second part is what to do when your system is under attack.
Below are the proactive steps you shall take to minimize the DDoS attack.
1. Using DDoS Protection Service
Buy a Dos/DDoS protection service that will detect abnormal traffic flows on your website and divert the traffic to another platform.

This will filter out the excess traffic sent onto your website and hence your network resources will remain unexhausted. Two such services are Cloudflare and Sucuri.
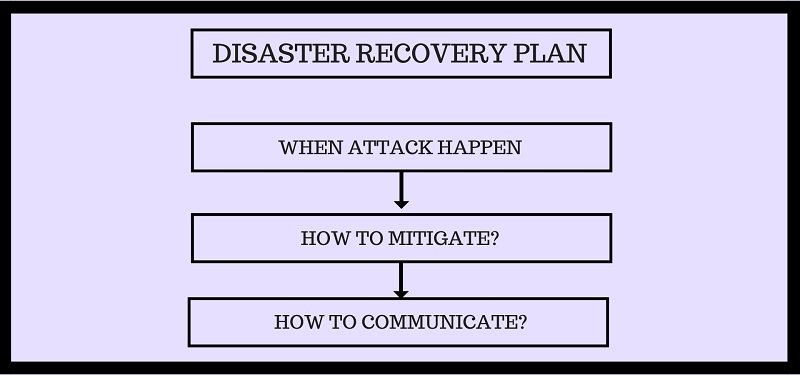
2. Disaster Recovery Plan
Develop a disaster recovery plan to ensure successful mitigation and communication when your website is under attack.
3. Secure System With Standard Protection Software
It is also important to secure your system from any form of malpractice done by an attacker by way of malicious and other backdoor programs.

For that, you need to regularly update and maintain good antivirus protection on all your devices. Moreover, install a firewall to restrict traffic incoming and outgoing from your website.
What to do when you are experiencing a DDoS attack. Now there are three approaches to mitigate a DDoS attack which are doing it yourself, outsourcing, and hybrid.
Tools to Protect from DDoS Attack
Here are the common tools used to perform and protect from DDoS attacks.
1. Tools Used by Attackers (Illegal and Strictly Punishable Crime)
There is a large pool of DDoS attack tools available on the internet. Most tools are freely available on the Internet. However, among these, LOIC and HOIC are commonly used by cybercriminals in launching a DDoS attack.
NOTE: The use of these tools to launch an attack on a public network is unethical and a crime.
2. Tools and Services Used for Protection
There are many tools and services available on the Internet such as Cloudflare, F5 Networks, Arbor Networks, Incapsula, Black Lotus, Akamai, AWS Shield, BeeThink Anti-DDoS Guardian, and Sucuri.
End Words
I hope this guide helps you understand everything about DDoS attacks. Did you learn something new from this guide? Or maybe you have a question. Either way, leave a comment below right now.
Further reading: Jobs and Careers in Cyber Security







![Cyber Security: An Ultimate Guide [2021]](https://techapprise.com/wp-content/uploads/2018/05/work-from-home-quotes-10-min-420x184.jpg)




